Create a GCP Kubernetes Cluster
Create the cluster
-
Access the Kubernetes Engine menu in the GCP console and select Clusters on the left-side menu.
-
Click CREATE.
For more information on creating a cluster, visit the Google Cloud documentation platform.
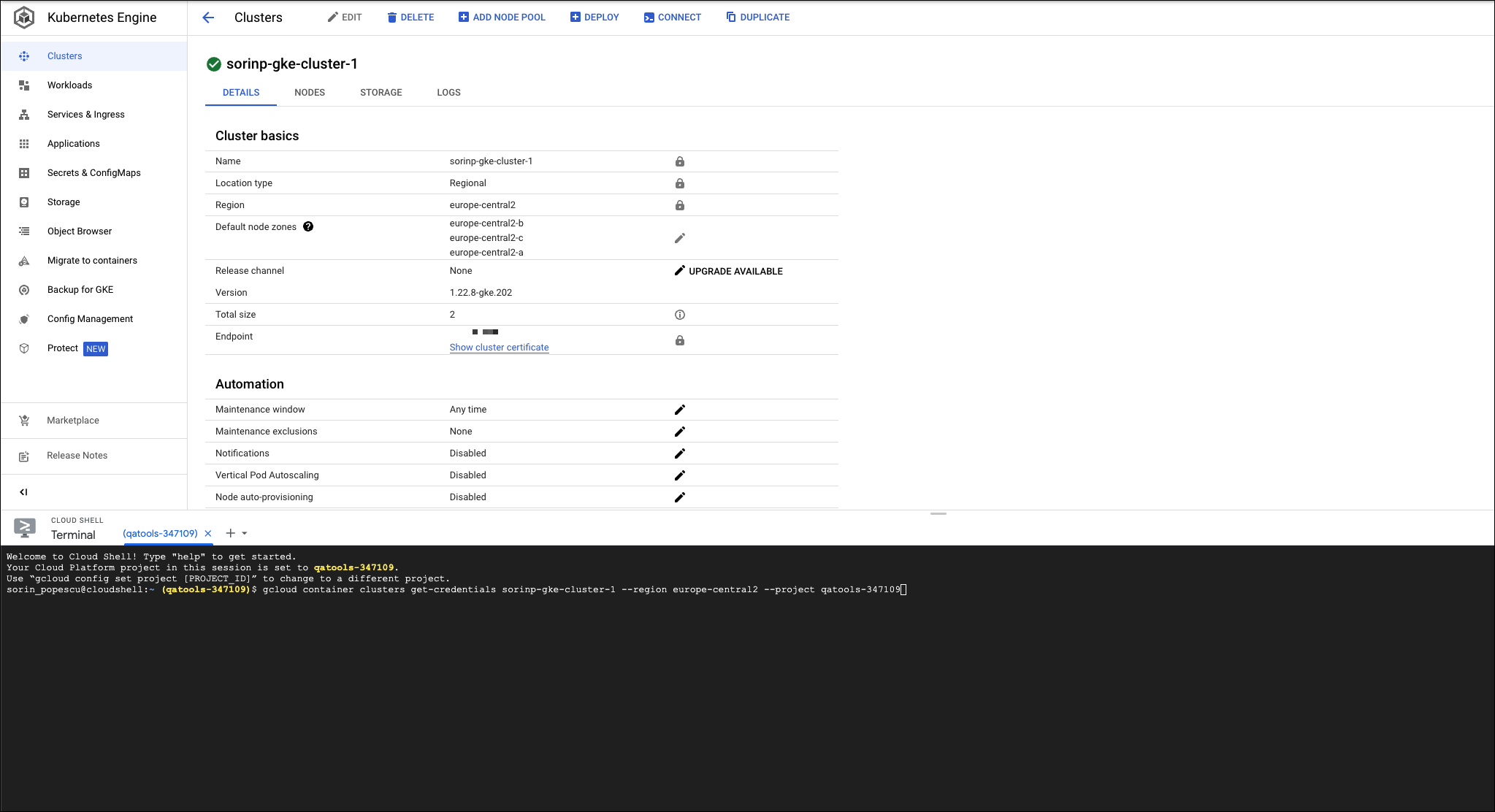
Retrieving the Cluster URL and the Cloud region
-
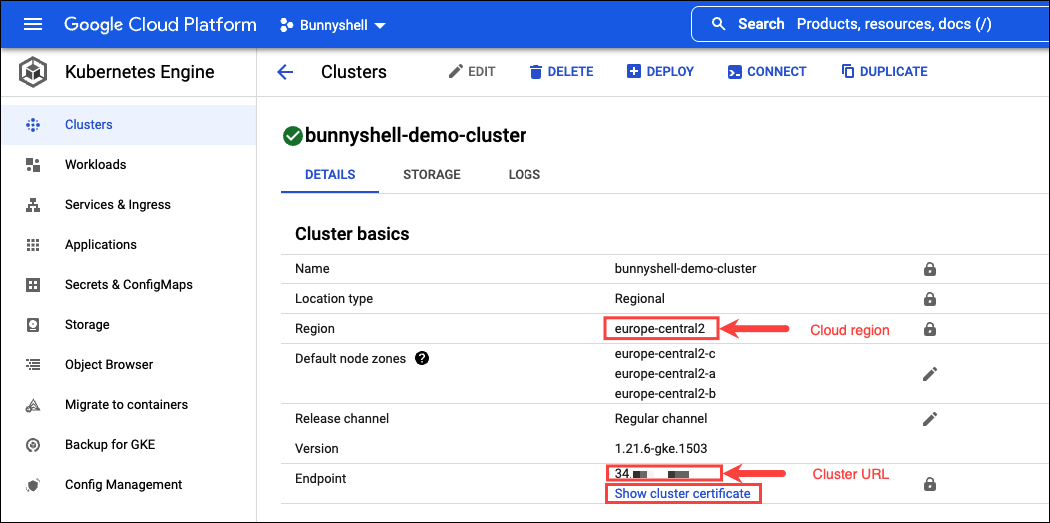
The Cluster URL and Cloud region can be fetched from the DETAILS screen when creating he actual cluster. You will need these two credentials later, when establishing the connection.
- The Cloud Region corresponds to the Region field in the DETAILS screen.
- The Cluster URL corresponds to the Endpoint field in the DETAILS screen.
Retrieving the Certificate
- Now we need to retrieve the Certificate. Click the CONNECT button.
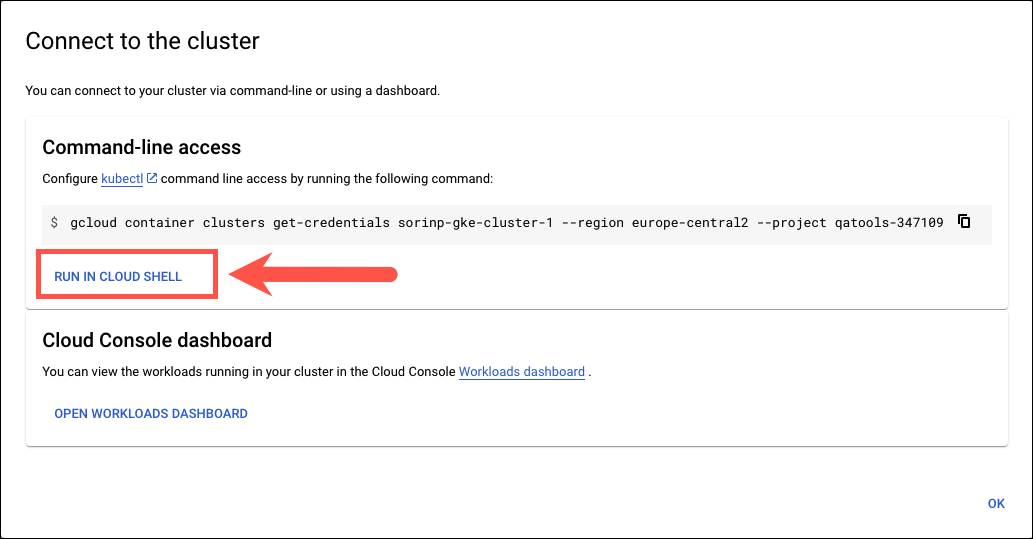
- Click RUN IN CLOUD SHELL.
- Approve any request.
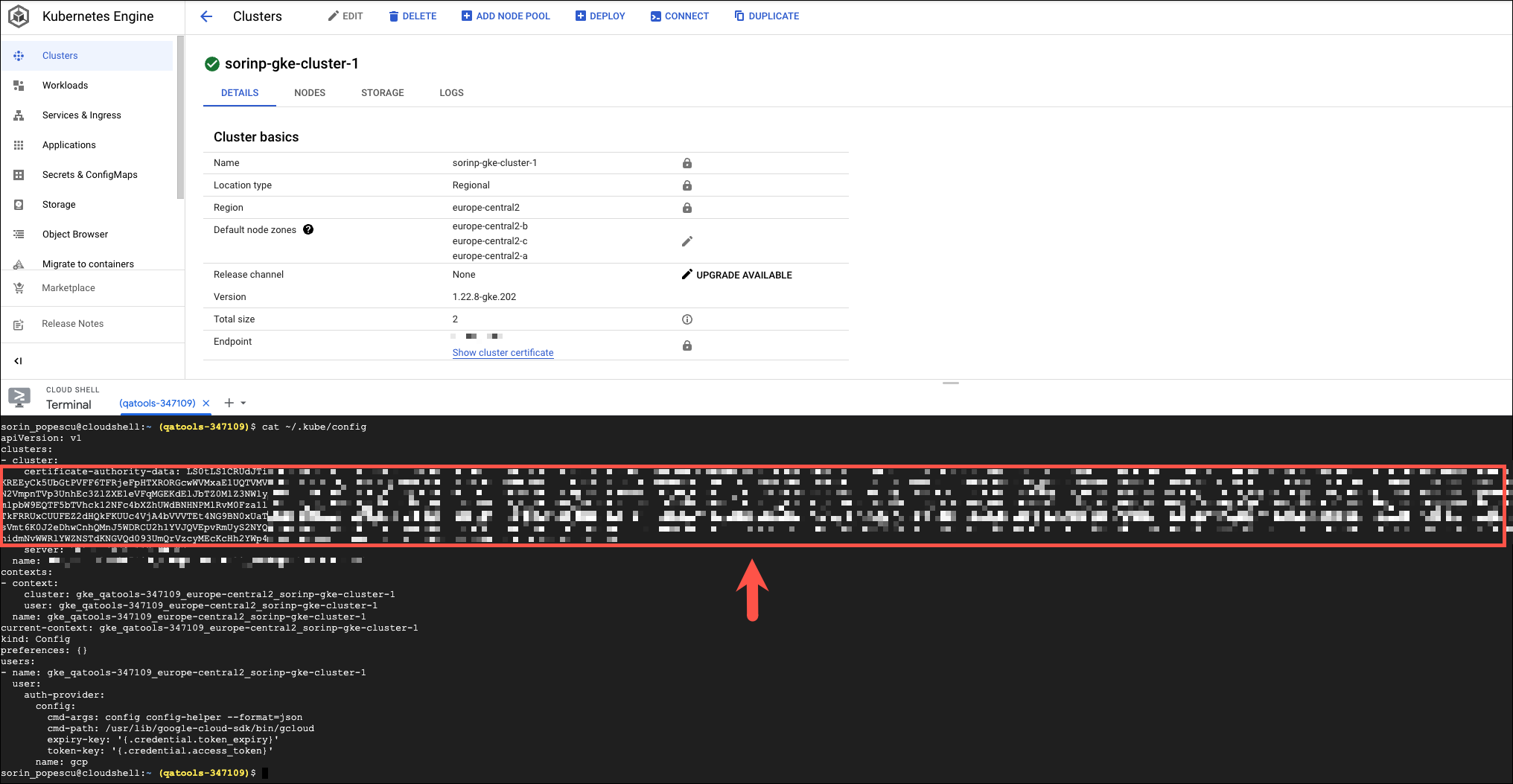
- Press Enter. Then type the following command:
cat ~/.kube/config- The Certificate corresponds to the
clusters.[...].cluster.certificate-authority-dataproperty. Copy it and save it for later use.
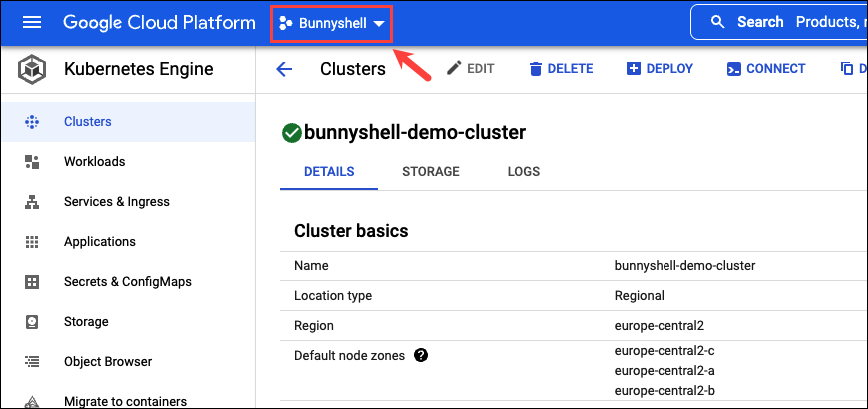
Retrieving the Cluster Project ID
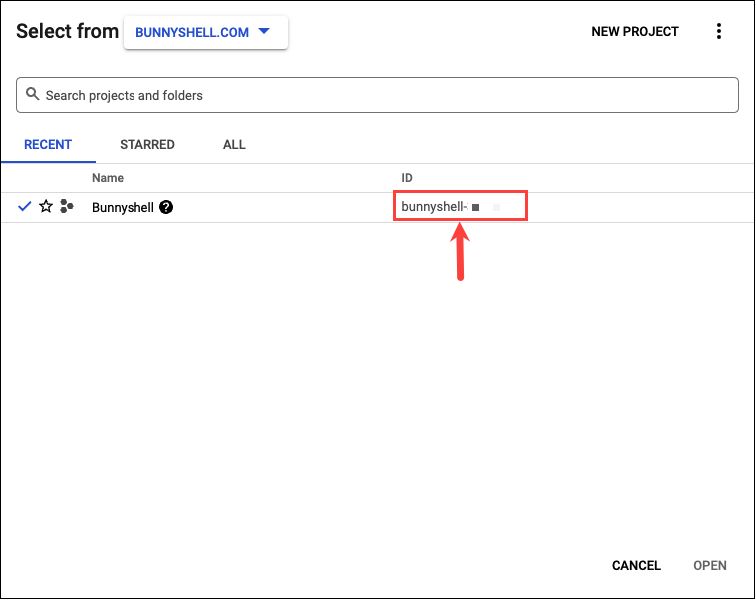
- The Project ID can be fetched by clicking on the {Project Name} in the top bar.
Grant access
Bunnyshell will have access to the cluster through a Service Account.
Prerequisites
You need to install the Google Cloud CLI and authenticate before moving to the next step.
Please see https://cloud.google.com/sdk/gcloud/reference/auth/login for more details.
Alternatively, you can perform these steps in Google Cloud Shell.
Creating the Service Account
Type the following command in the Google Cloud CLI to create the Service Account:
gcloud iam service-accounts create {USER}Example
gcloud iam service-accounts create bunnyshell-access
Grant the Service Account access to your cluster
Then type the following command to grant the Service Account access to your cluster:
gcloud projects add-iam-policy-binding {PROJECT_ID} \
--member=serviceAccount:{USER}@{PROJECT_ID}.iam.gserviceaccount.com \
--role=roles/container.adminExample
gcloud projects add-iam-policy-binding bunnyshell-347109 \
--member=serviceAccount:[email protected] \
--role=roles/container.admin
Retrieve the Google Service Account Key
Finally, type this command to create a key for your Google Service Account
gcloud iam service-accounts keys create gsa-key.json \
--iam-account={USER}@{PROJECT_ID}.iam.gserviceaccount.comExample
gcloud iam service-accounts keys create gsa-key.json \
--iam-account=bunnyshell-access@bunnyshell-347109.iam.gserviceaccount.comUpdated 6 months ago
